We have seen many companies ask these types of questions through a Request for Information, prior to issuing a more detailed Request for Proposal (RFP). To get started building your custom RFP, best fit for your needs, check out the template we created to help companies like you.
White Paper Global ITAD
Building a Successful Global IT Asset Disposition Program
IT equipment today is the lifeline of any business, and while upkeep and proper maintenance is important, it is not easy. From maintenance and upgrades to final disposition, each phase of managing the lifecycle of IT assets within an organization presents its own set of unique challenges.
Similar to IT asset management (ITAM) processes within an organization, the IT asset disposition (ITAD) process has matured in recent years. Companies have begun to understand data security and environmental compliance risks associated with disposition programs that do not follow rigorous processes. This is why over the last few years Sims Lifecycle Services (SLS) has seen many global RFPs as companies started recognizing their own inconsistent ITAD programs at their locations around the world.
Wondering where to start?
It does not always have to be as drastic as tearing up your current ITAD program, and starting over; although that may be necessary in some cases. Start first by assessing your current situation, then understanding where you can improve to ensure your program will be successful.
“ITAD service providers have become an important link in the overall technology life cycle management of IT equipment. Without a thorough, detailed end-to-end process that is consistently executed throughout your enterprise, ITAD too often becomes an afterthought that carries significant risks.”
Noted Gartner, Inc in the Gartner Market Guide for IT Asset Disposition, January 2023.
Assessing the Situation
Perhaps you are unsure if your ITAD and electronics recycling program could be vulnerable to security threats. The following checklist will help you understand your program’s current strengths and weaknesses, allowing you to create an action plan for improvement.
Do any of these sound familiar?
- I have no clear audit trail for corporate and regulatory compliance (Regulatory Environment)
- I have insufficient/no visibility into data destruction, chain-of-custody (Corporate Policies)
- I do not have consistent asset reports, invoices, or certificates of data destruction (Corporate Policies)
- My disposal program is not aligned to our corporate risk management program (Corporate Policies)
- I do not have a defined process for securely handling data bearing equipment (Corporate Policies)
- It is difficult for me to get accurate asset lists from different locations (Operations)
- I have trouble determining asset condition, count, and age for each location (Operations)
- I have an IT asset disposition (ITAD) process that is different from other locations. (Operations)
- I have inconsistent billing and no overall visibility of total costs (Operations)
- I have no guidance on how to manage retired IT assets within our corporate data privacy program. (Operations)
- I do not have a line item in my budget to manage my ITAD program, or for asset disposition activities. (Operations)
- I manage multiple vendors who were onboarded years ago with regional vs. global focus (Vendor Selection)
- My current vendors cannot fulfill all of my needs I have today (Vendor Selection)
If you checked any box off this list, you should review, update and add to your ITAD program plan. Use the following chart to determine what areas you want to focus on the most.
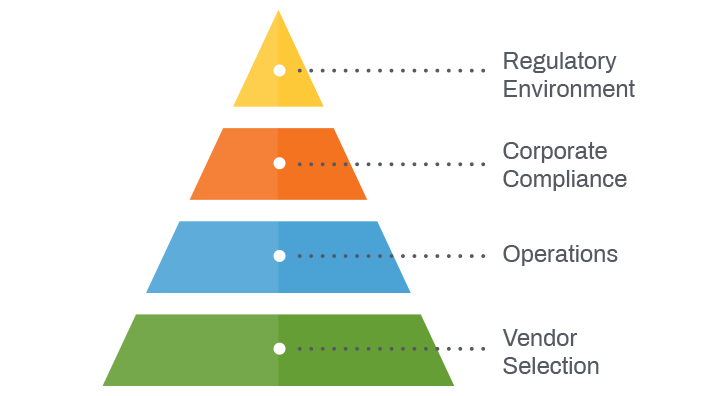
Regulatory Environment (1 in the list above)
Companies must adhere to data security and environmental legislation in the macro environment. Globally this regulatory framework is typically by country or region.
Corporate Compliance (2 – 5 in the list above)
ITAD programs should be consistent with a company’s risk management and data security policies.
Operations (6 – 11 in the list above)
Many global companies are restructuring ITAD programs to be centrally managed and consistent at locations worldwide.
Vendor Selection (12 – 13 in the list above)
The breadth and depth of services offered by ITAD and electronics recycling vendors vary dramatically. It is important to select a vendor who has capabilities that best match your requirements.
*A more detailed discussion for each of these four segments follows.
Regulatory Environment
Global Data Privacy Regulations
European Union (EU)
In May 2018, the EU’s General Data Protection Regulation (GDPR) came into effect. GDPR is a data privacy regulation in Europe that outlines significant financial penalties for non-compliant handling of EU citizens’ data.
It does not matter where you are based, where you do business or where your headquarters is located. If your company handles, processes or stores data of EU citizens, you need to be GDPR compliant. The consequences of non-compliance are severe. Companies can face fines of up to €20,000,000 or four percent of global revenue.
The UK Data Protection Act (DPA) 2018 implements the GDPR with several additions and restrictions.
The revised Swiss Federal Act on Data Protection 2020 (FADP) expands the definition of sensitive personal data by including genetic and biometric data.
United States (US)
In the US, there is no federal legislation but instead a patchwork of state-by-state legislations including:
- Californian Consumer Privacy Act (CCPA) which extends privacy protections to the internet.
- Nevada’s Senate Bill 220, or “An Act relating to Internet privacy,” will require operators of internet websites and online services to follow a consumer’s direction not to sell his or her personal data.
- The Maine privacy law—“An Act to Protect the Privacy of Online Customer Information”— focuses entirely on user data collected by Internet Service Providers (ISPs).
- The Health Insurance Portability and Accountability Act (HIPAA) of 1996 which protects healthcare patient data.
- The Gramm-Leach-Bliley Act (GLBA) and the Fair and Accurate Credit Transactions Act (FACTA) which are directed at financial institutions.
- The Payment Card Industry Data Security Standard (PCI DSS) which applies to companies who accept credit card payments.
- The Family Educational Rights and Privacy Act (FERPA) legislation that protects the privacy of students by ensuring their education records are protected.
- The Federal Trade Commission Act (FTC Act) monitors apps and websites that violate their own privacy policy.
- The Fair Credit Reporting Act (FCRA) covers information in your credit report. It limits who is allowed to see a credit report, what the credit bureaus can collect, and how information is obtained.
- In 2023, ten US states (Oregon, Florida, Delaware, Texas, Montana, Tennessee, Indiana, Iowa, Virginia and Colorado) created new data privacy laws or amended existing laws.
Brazil’s Lei Geral de Proteção de Dados (LGPD) is a comprehensive data protection law built on the EU’s GDPR.
Canada’s PIPEDA is a federal law that governs the data collection, processing, and protection by federal works or businesses operating within Canada.
APAC
In 2021, China enacted its main data protection regulation, the Personal Information Protection Law (PIPL). PIPL applies to organizations that are providing services within China or processing personal information of Chinese citizens from within or outside the country.
China’s Data Security Law (DSL) regulates data processing activities by organizations and individuals, as well as security supervision of such activities within China.
Thailand’s Personal Data Protection Law (PDPA) aims to guarantee the protection of individuals’ personal data and regulate businesses that deal with the collection, usage, and disclosure of personal data.
The Australia Privacy Act includes 13 Australian Privacy Principles (APPs), which apply to private sector organizations, as well as most Australian Government agencies.
Japan’s APPI regulates personal related information and applies to any Personal Information Controller (PIC) providing personal related information for use in business in Japan.
With so many tightened data security requirements, companies are taking steps to develop more structured and formalized ITAD programs that are compliant with industry and privacy legislation and corporate risk management programs.
Global E-Waste Legislation
Legislation governing how e-waste is disposed of is inconsistent regionally and globally. Batteries, toner, ink, mercury bulbs and leaded glass from CRT monitors are common items requiring special handling when recycling electronics.
There have been significant industry issues with e-waste being illegally exported and dumped in developing countries causing human health and environmental issues. With the patchwork of inconsistent legislation, most companies take their own proactive stance in auditing vendors to ensure e-waste disposal is managed responsibly.
The International Electrotechnical Commission (IEC) is preparing a new standard, IEC 63395, which aims to facilitate the systematic, sustainable management of e-waste. Among its objectives, it seeks to reduce the amount of e-waste sent for disposal through reuse and recovery, prevent the inappropriate disposal of e-waste and restrict operators who do not comply with the standard or comparable requirements from receiving e-waste shipments.
Evaluating Regulatory and Corporate Requirements
Regulatory compliance efforts can be further complicated when companies operate in multiple locations and face regulations that vary by country. For global ITAD, questions that typically come up include:
- What industry regulations need to be considered in each country regarding data privacy?
- Is there legislation regarding e-waste disposal?
- What changes on the horizon may affect how you dispose of e-waste?
- Are there any industry regulatory changes in the countries you operate, that impact your ITAD program?
Corporate Compliance
Corporate Management Considerations
Corporate risk management, business continuity, and data security policies can all impact your global ITAD program. A data destruction plan for media storage devices is critical when removing IT equipment and electronic assets from your live environment. This should reflect the same risk protection as outlined in your corporate data security policies.
Looking Back
ITAD regulations and requirements have evolved with the emerging electronic world. What was once thought of as merely a disposal exercise has now become an integral part of a corporation’s security, financial, compliance and sustainability policy.
As data risks became more publicized and data threats more intimidating, companies began dedicating resources to ensure data destruction of information stored on retired IT assets. Companies have a vested interest in protecting confidential corporate information such as trade secrets, sales records, copyright and intellectual property, as well as customer data.
Global companies often face the challenge of consistently managing data destruction processes from country to country at smaller offices with remote employees.
In addition to managing inventory, these global companies must also consider changes to data bearing devices over time. For instance, it took several years for all-in-one copiers and printers to be recognized as “data bearing devices” after they were equipped with hard drives to support electronic document storage.
The continual emergence of robotics, augmented reality, virtual reality and the Internet of Things (IoT) has resulted in a rapidly and continually growing network of connected objects that are able to collect and exchange data in real time. Thermostats, cars, lights, appliances, watches and even entire homes can all be connected to the IoT.
Insider Intelligence predicts that there will be 4.3 billion IoT mobile connections worldwide by 2026 and more than 64 billion IoT devices installed by 2026. There are literally billions of devices in the world that contain personally identifiable information.
Notes Gartner in their 2023 Market Guide for IT Asset Disposition: “The rapid growth of “smart” devices, along with the exploding volume and variety of connected Internet of Things devices, is forcing a reevaluation of traditional ITAD processes by both users and providers alike”.
After removing data bearing assets from your live environment, it is important to have a plan in place to ensure all data is destroyed.
Operations
Overview of an ITAD Program
Companies are taking a closer look at the infrastructure of vendors providing ITAD and e-waste recycling services. Having a better understanding of their overall ITAD vendor capabilities and capacities will help ensure their corporate interests are protected and are compliant with relevant regulations.
Fragmented ITAD and Computer Recycling Programs
Some large enterprises manage ITAD independently at each company location. Too often, ITAD responsibilities have not been part of anyone’s job description nor provided in any formalized manner. This fragmented opaque approach is no longer acceptable today. A detailed understanding of your company’s IT landscape is key to developing an ITAD program that aligns with the management of your company’s compliance and data policy risk. An experienced ITAD vendor will not only be able to support your current program as it exists but will be able to work with you to improve and optimize your process.
Know What You Have — Operational Challenges for Multi-site Locations
The first obstacle many companies face in trying to manage a global ITAD program is a black hole of information. It can be difficult to assess what assets you have, where they are located and how each location handles removing IT assets from your live environment.
It is difficult to manage what you cannot measure.
Common challenges include:
- Ad-hoc approach at each facility,
- Inconsistent and undocumented processes,
- Undefined job description/ownership,
- No central control or reporting,
- Lack of training
- Multiple vendors (and multiple ways of doing things).
Vendor Selection
Global Data Privacy Regulations
The ITAD services required at each location will vary by client. In general, services offered by IT asset disposition industry providers are categorized by location, either at the:
- Client’s location (on-site services), or
- Vendor facility (off-site services).
Moving IT assets between two locations is also important for full accountability, especially for any data bearing devices. This diagram provides an overview of the structure of a typical ITAD program.
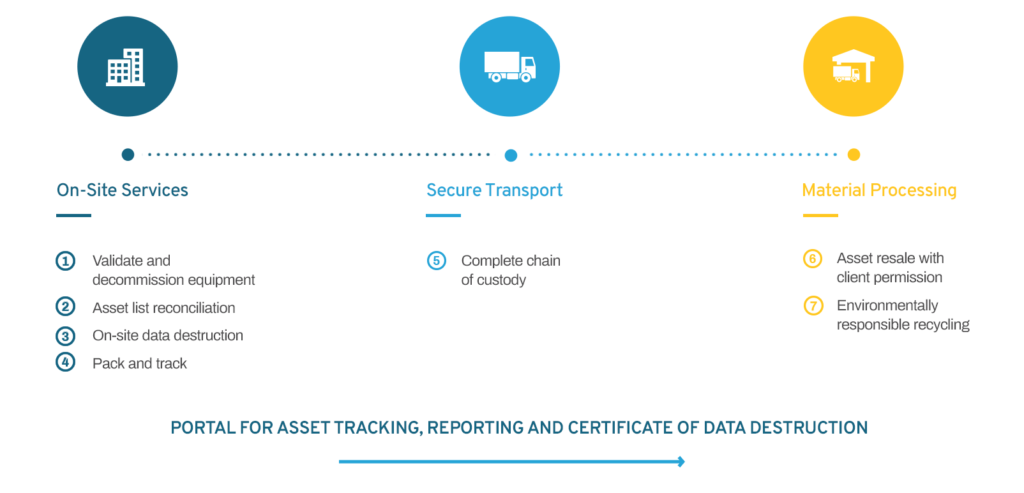
On-site ITAD services (at client location) include:
- Decommissioning of IT assets
- Secure asset storage (between vendor pickups)
- Data destruction
- Inventory reconciliation (verification of make, model, serial number and asset tag, cross-referenced to internal lists)
- Packing of IT assets
It is important to know the correct transport service is provided to ensure chain-of-custody is defined, known and consistent with the risk associated with assets to be transported.
Off-site services (at service provider location) includes:
- Data destruction (if not done at client location)
- Resale of IT assets
- Redeployment of IT assets within your organization
- Parts harvesting (if applicable)
- Recycling
- Reporting
At a high level there are other vendor qualifications and capabilities to consider. To ensure credibility of the business you should consider the company size, longevity, number of employees and understand what percent of their business is dedicated to ITAD services.
When it comes to execution, you can ask yourself these questions about an ITAD vendor.
- Do they have the infrastructure to support a global program?
- Does their footprint align to our footprint?
- How do they “fill in gaps” for services they do not provide directly?
- Can they demonstrate they can provide systematic and secure support?
- Can they support our data destruction requirements?
- Are they familiar with country regulations for handling data? E-waste? Billing?
- Do they operate to industry standards?