How to manage hardware security when decommissioning a hyperscale data center
Physical IT security is important in ensuring the prevention of data from being compromised in a physical way. In a recent report, 63 percent of organizations reported security breaches over the last year due to hardware vulnerabilities, and only 59 percent of those companies had an implemented hardware security strategy. These vulnerabilities have become a target as cybercriminals face stronger security precautions and technologies by other means.
As data threats increase, many are looking to prioritize integrating methods for improving physical security during server decommissioning. Here are five things you can do to manage secure data center decommissioning.
1. Track and Report on all Inventory
Strong IT asset inventory lists can be the backbone of an IT asset disposal and decommissioning program. If a data center manages an updated asset inventory list, ideally mapped by grid, coordinate, software, hardware and more, the vendor can map out their job and provide a more accurate estimate of how long the process will take. Ongoing management of an IT asset inventory list helps ensure all items are accounted for, all assets can be located by tracking cabinet and rack slot, and can later be referenced when tracking disposition.
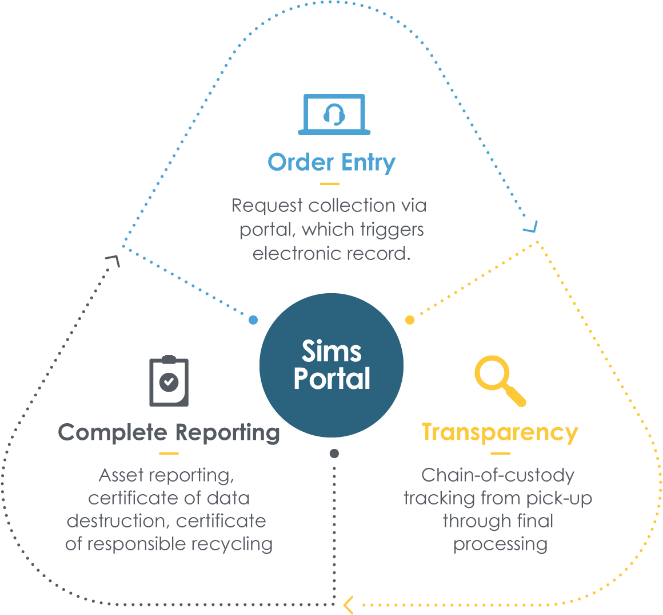
Keeping that list up to date and managing data destruction for every data storage device is where execution and daily management can become a challenge. IT asset disposition (ITAD) portal systems are useful for managing this information. Recorded details might include make, model, serial number, and how and when the asset was reused or redeployed. ITAD vendors usually offer this as a part of their service and Sims Lifecycle Services (SLS), in particular, can offer multiple currencies and additional data capture for clients with unique requirements.
The SLS portal system can support pickup requests, asset tracking, asset resale through e-commerce, reporting and certificates of data destruction.
2. Place Data Storage Devices in Caged-Off Areas
The use of strong and secure server cages in data centers can keep data safe and separated at all times. Security cages can be effective in securing the entrance to a computer server room or area where there is stored IT equipment.
When replacing servers you need a secure process when removing assets from a storage area as well. Many utilize locked storage containers for hard drives or storage devices, so they can be securely transported offsite for data destruction or removal. In some cases onsite shredding or data wiping may take place prior to being sent to an ITAD site for further processing.
3. Perform Data Destruction On-Site
On-site data destruction services have become useful for providing a secure option for hard drives prior to being removed from a site. Witness destruction options can also enable you to view the physical destruction of these devices as it takes place, and before equipment is transported away for recycling, providing proof of data security.
If equipment is being reused, data wiping should be performed by a professional certified data destruction vendor who can wipe according to industry guidelines for media sanitization. Two wiping standards often used in the industry include, NIST SP 800-88 r1 in the United States, and HMG IA Infosec No5 in the United Kingdom.
Additional strategies tend to be unique to each organization and their needs. Working with a professional to perform data destruction services at your data center is how many can successfully manage IT security.
4. Utilize IT Smart Hands Services
A smart hands service is a great option to utilize if you require on-site technicians. These specialized ITAD technicians manage data destruction of replaced or unused servers, storage or network equipment. These services are intended to be a less-expensive alternative to hiring certified technicians, and provide an option for a specialized and compliant service that can be utilized 24/7.
These services generally include,
- inventory control,
- data destruction,
- IT resale or redeployment, and
- electronics recycling.
Utilizing smart hands services can offer full-time accountability for assets, compliance with applicable regulatory requirements, and environmentally responsible disposition.
5. Consult with the Experts
When managing IT asset disposition and data center decommissioning services each company has unique needs and requirements. From a global perspective, when managing assets in different locations around the world, regulations will vary by region/country. Having a strategic advisor for global ITAD available to help guide you on regulations and legislation, will offer a great impact on the overall integrity of your program.
ITAD and security done well go hand in hand. Lack of expertise, general carelessness, and unexpected delays can result in a higher cost than just unrecovered value. Ultimately, IT asset disposition is only as effective as the safeguards you put in place and the vendors you choose.
Additionally, ensuring a smooth vendor transition is important to ensure you are receiving the service you signed up for.
GUIDE: Managing a Smooth Transition to a New Global ITAD Service Provider
6. Go Beyond Industry Standards
There are several industry standards in place globally, that can be a great reference for identifying key players. Ensuring general industry requirements and standards are met is important, but to take things a step further you can also expand on this.
Look for ways to understand your vendor’s security framework and protocols for risk mitigation. If possible, it is best to visit the site in person. If that is not an option at this time, virtual tours have become a great way to get a feel for the operation.
Beyond ITAD security certifications: What you need to look for blog
An estimated 32 percent of IT budgets are projected to be dedicated to the cloud by 2021, leaving cloud providers with increasing demands and expectations. Gartner experts shared what they consider the three greatest risks within the ITAD process. These risks included data sanitization, transportation logistics, and recycling.
Spending time and budget on ITAD security in your data center will play more of a role in keeping your business, and its stored data, protected.
